- Entry-Level
- Mid-Career
- Senior-Level

Information Security Analyst Text-Only Resume Templates and Examples
Jessica Morrison
(123) 456-7890
[email protected]
123 Your Street, Philadelphia, PA 12345
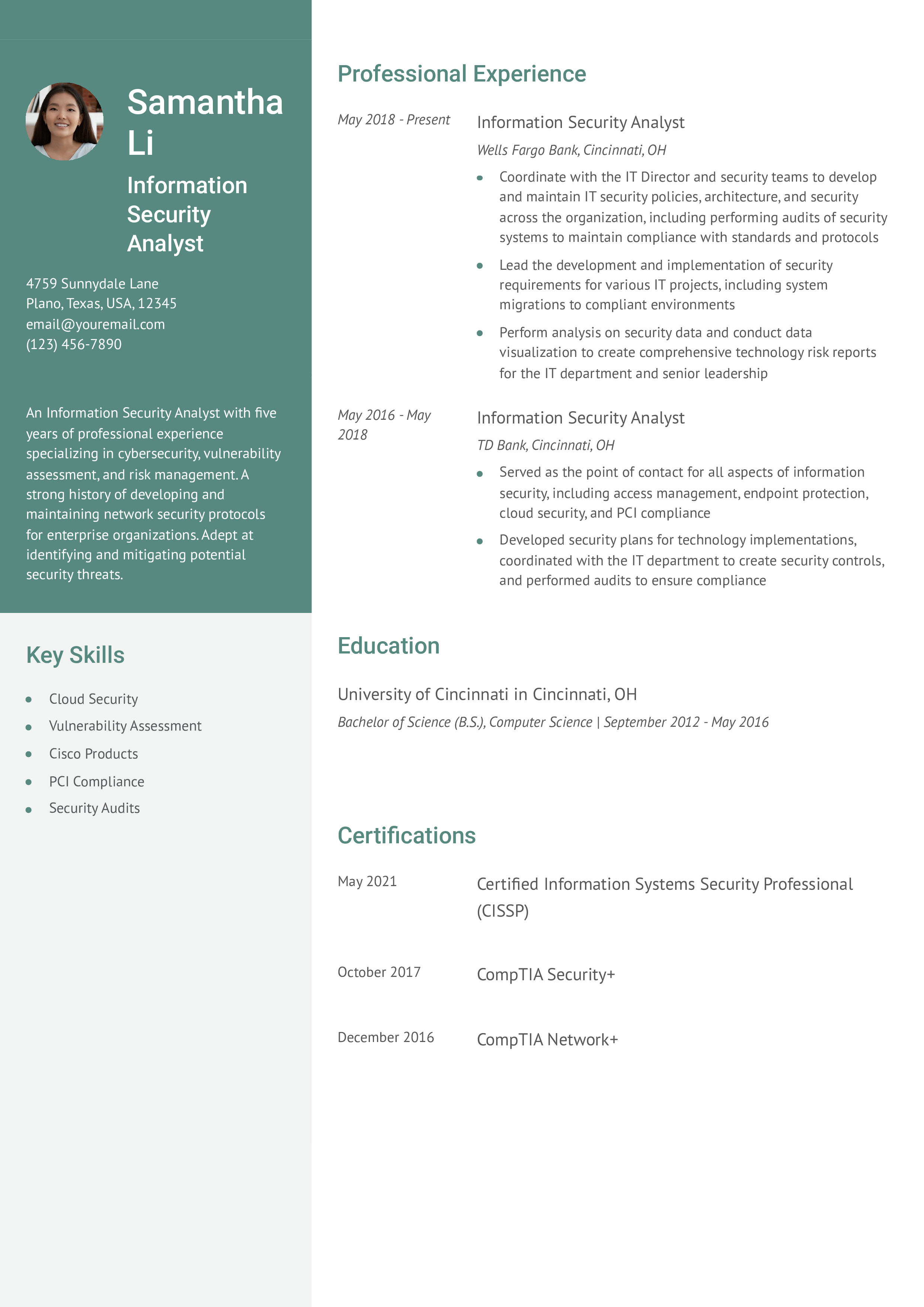
A Senior Information Security Analyst with 10+ years of experience within the healthcare industry, specializing in SIEM, cybersecurity, and security assessments. A strong history of leading cloud deployments and security assessments to ensure confidentiality and integrity of patient data for large hospitals and healthcare organizations.
Professional ExperienceInformation Security Analyst, Penn Medical Center, Philadelphia, PA
October 2016 – Present
- Provide subject matter expertise to project teams for cloud and on-site deployments, including developing system security plans, conducting testing on security controls, and performing vulnerability assessments to ensure HIPAA compliance
- Partner with technology teams to enhance access management protocols and improve the user experience for 500+ employees
- Coordinated with data governance teams to ensure confidentiality of medical records, including leading the implementation of new security protocols
Information Security Analyst, Jefferson University Hospital, Philadelphia, PA
May 2014 – October 2016
- Oversaw all aspects of network security, threat prevention, and incident reporting systems, identified root causes of security threats and intrusions
- Delivered training to 100+ team members on security protocols and best practices, which included creating training materials and assets
Bachelor of Science (B.S.) Computer Science
Drexel University, Philadelphia, PA September 2010 – May 2014
- Cybersecurity
- HIPAA Compliance
- Network Security
- Threat Prevention
- PCI Compliance
- Certified Information Systems Auditor (CISA), 2019
- Certified Information Systems Security Professional (CISSP), 2019
- CompTIA Security+, 2014
How To Write an Information Security Analyst Resume
To write a compelling information security analyst resume, feature your experience mitigating security threats, ensuring data integrity, and performing vulnerability assessments. Demonstrate your comprehensive knowledge of cybersecurity, industry regulations, and security standards using tangible examples from your career. This guide provides expert tips and insights to help you build an accomplishment-driven resume and land your next big job opportunity.
1. Write a brief summary of your information security analyst qualifications
Lead your resume with a strong opening summary that captures your strongest qualifications as an information security analyst. Start with a sentence that lists your title, years of experience, and three to four security-related skills that match the job description. In the subsequent sentences, emphasize the nuances of your industry expertise.
For example, mentioning that you’ve developed cybersecurity policies or protocols for enterprise organizations in the past is a great way to establish your credibility as a subject matter expert. Remember, the goal is to provide an engaging snapshot of your career that draws the hiring manager in and entices them to read further.
Profile Example #1
An Information Security Analyst with five years of professional experience specializing in cybersecurity, vulnerability assessment, and risk management. A strong history of developing and maintaining network security protocols for enterprise organizations. Adept at identifying and mitigating potential security threats.
Profile Example #2
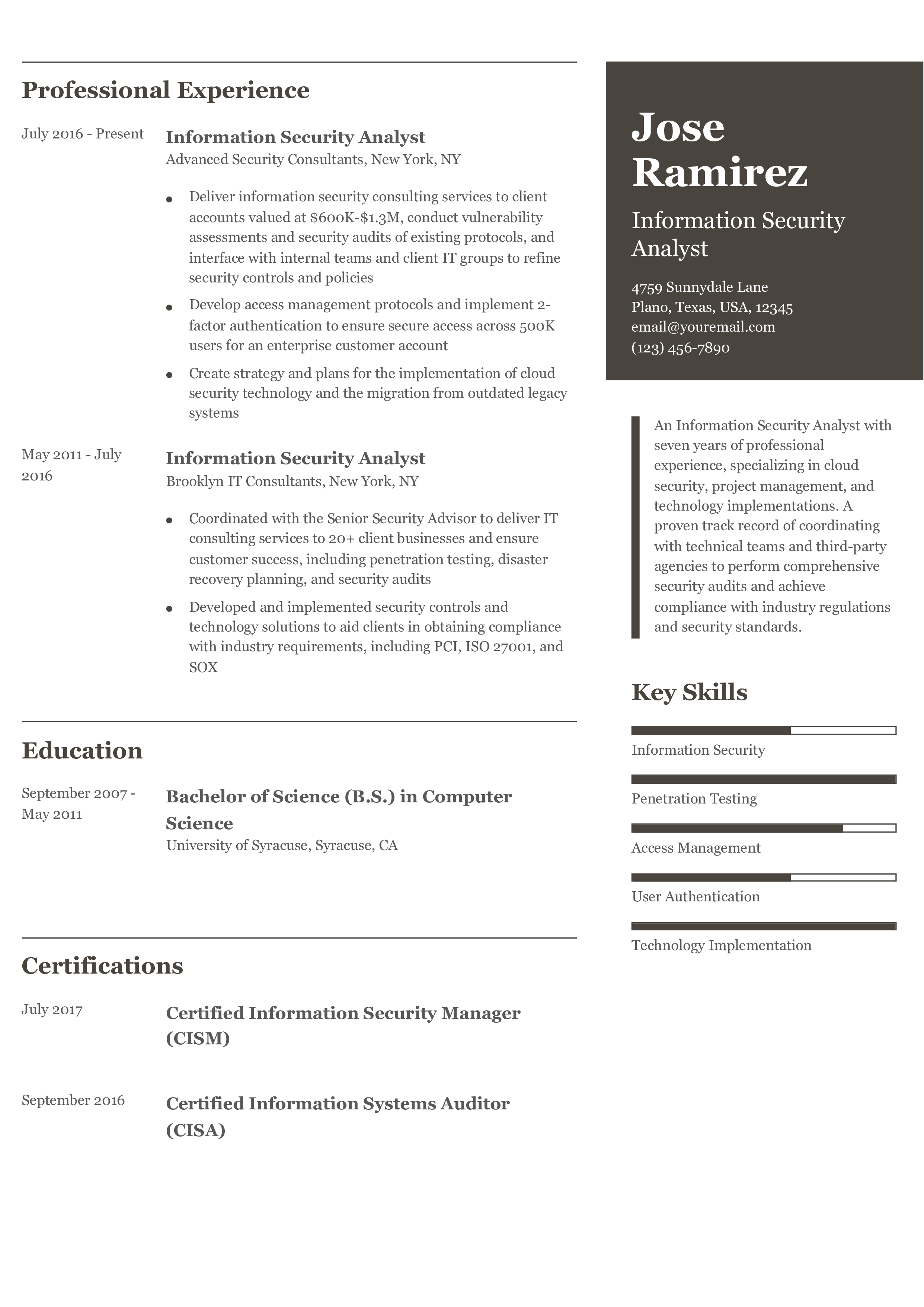
A Senior Information Security Analyst with 10+ years of experience within the healthcare industry, specializing in SIEM, cybersecurity, and security assessments. A strong history of leading cloud deployments and security assessments to ensure confidentiality and integrity of patient data for large hospitals and healthcare organizations.
2. Showcase your information security analyst experience
Incorporating key metrics and monetary figures from your work experience into your bullet points can significantly enhance the impact of your professional accomplishments. Although it may be challenging to identify appropriate numbers when dealing with information security, it’s important to show the effect of your contributions.
For example, if you automated an incident response procedure, you might incorporate data that showcases a cost reduction or increase in response time. Providing specific metrics from your career will also mitigate the risk of your document appearing generic and paint a clearer picture of your experience.
Professional Experience Example #1
Information Security Analyst, Wells Fargo Bank, Cincinnati, OH May 2018 – Present
- Coordinate with the IT Director and security teams to develop and maintain IT security policies, architecture, and security across the organization, including performing audits of security systems to maintain compliance with standards and protocols
- Lead the development and implementation of security requirements for various IT projects, including system migrations to compliant environments
- Perform analysis on security data and conduct data visualization to create comprehensive technology risk reports for the IT department and senior leadership
Professional Experience Example #2
Information Security Analyst, Penn Medical Center, Philadelphia, PA October 2016 – Present
- Provide subject matter expertise to project teams for cloud and on-site deployments, including developing system security plans, conducting testing on security controls, and performing vulnerability assessments to ensure HIPAA compliance
- Partner with technology teams to enhance access management protocols and improve the user experience for 500+ employees
- Coordinated with data governance teams to ensure confidentiality of medical records, including leading the implementation of new security protocols
3. Add your information security analyst education and certifications
In addition to your degree, several certifications can be relevant to a job in the information security analyst field. For example, the Certified Information Security Manager certification (offered by the Information Systems Audit and Control Association) proves expertise in information security management. Similarly, the Certified Information Systems Security Professional (CISSP) is one of the most widely recognized certifications and covers a wide range of topics.
These certifications can help you stand out from other candidates when applying for jobs in the information security analyst field, but other types of certifications may be relevant depending on the specific job. Be sure to include any that may be useful to potential employers, even if they’re not required for the position.
Education
Template
- [Degree Name]
- [School Name], [City, State Abbreviation] | [Graduation Year]
Example
- Bachelor of Science (B.S.) Computer Science
- University of Syracuse, Syracuse, CA September 2007 – May 2011
Certifications
Template
- [Certification Name], [Awarding Organization], [Completion Year]
Example
- Certified Information Systems Security Professional (CISSP), the Information System Security Certification Consortium | June 2012
- Certified Information Security Manager, Information Systems Audit and Control Association | April 2015
4. Make a list of your information security analyst-related skills and proficiencies
To secure interviews during your job search, incorporate key skills and action verbs that match the needs of prospective employers. Tactically integrate keywords from the job description into your resume, ensuring your document is appropriately optimized for applicant tracking systems (ATS). This strategy will also help differentiate you from the field of applicants and grab the hiring manager’s attention. Be sure to include specific examples of using these skill sets throughout your career to demonstrate your hands-on experience.
Below is a list of key skills and action verbs you may encounter during your job hunt.
| Key Skills and Proficiencies | |
|---|---|
| Access management | Cloud security |
| Cloud technology | Compliance |
| Cybersecurity | Data analysis |
| Data analytics | Endpoint protection |
| Firewalls | Information security |
| Information technology (IT) | ISO 27001 |
| IT security | MySQL |
| Network security | Payment Card Industry (PCI) compliance |
| Project management | Python |
| Risk management | Root cause analysis |
| Security audits | Security controls |
| Security information and event management (SIEM) | Software Development Life Cycle (SDLC) |
| Top secret clearance | Transmission Control Protocol/Internet Protocol (TCP IP) |
| User authentication | Vulnerability assessment |
How To Pick the Best Information Security Analyst Resume Template
When selecting your information security analyst resume template, prioritize structure, readability, and organization over aesthetics. Avoid distracting visual elements, flashy colors, and graphics that might draw the reader’s eye away from your content. Opt for an elegant, single-column template that allows you to control the flow of information and reorder your sections according to your career needs.
Frequently Asked Questions: Information Security Analyst Resume Examples and Advice
Can I adjust an Information Security Analyst resume example for different roles or industries?-
Yes, you can easily adjust an Information Security Analyst resume example by aligning your profile summary and key skills with the job description. If you are applying to different industries, emphasize transferable skills and any industry-specific experience. For example, if you’re applying to a finance role after working in tech, highlight your data analysis and financial reporting skills as relevant to both fields.
What are common action verbs for information security analyst resumes?-
One of the most common resume mistakes is using too few verbs. You may repeat the same generic verb (say, “manage”) many times or rely on passive phrases like “responsible for” or “accountable for.” These tendencies can distract your reader and fail to show the dynamic nature of your work.
The following list will help you mix up the verbs on your information security analyst resume:
| Action Verbs | |
|---|---|
| Analyzed | Built |
| Conducted | Coordinated |
| Created | Designed |
| Determined | Developed |
| Diagnosed | Evaluated |
| Examined | Identified |
| Implemented | Improved |
| Oversaw | Planned |
| Resolved | Spearheaded |
| Supported | Tested |
How do you align your resume with an information security analyst job description?-
According to the Bureau of Labor Statistics, the average annual salary for information security analysts was $112,000 in May 2022. These positions are expected to grow by 32% from 2022 to 2032, much faster than the average for all occupations. Despite the many opportunities available, you’ll still face considerable competition in your job hunt. Be sure to carefully align your resume with each position you apply for.
For example, if you’re applying for an information security analyst role with a health care organization, emphasize your background overseeing access management protocols and data confidentiality. If a company is seeking a candidate with a strong knowledge of cloud security, feature examples of you leading cloud deployments and migrations.
What is the best information security analyst resume format?-
When creating a resume for a security analyst job, choosing a format that highlights your skills and experience in the industry is important. The reverse chronological format is the most commonly used format and is ideal for those with a solid work history in the industry. This format lists your work experience in reverse chronological order, starting with your most recent job and working backward. It also includes traditional elements of a resume, like work history, education, and contact information.
What’s the recommended length for an information security analyst resume?-
The recommended length for an information security analyst resume is one page, especially for professionals with under 10 years of experience. A two-page resume can work for those with substantial accomplishments or a longer career, but only if it’s concise and highly relevant to the role. Tailoring your resume to the job and highlighting your strongest qualifications are key to success.
Stick to listing work experience from the last 10 to 15 years, as this period is most relevant to employers. Summarize or omit older positions unless they’re crucial for your application. A focused and streamlined resume will help capture the hiring manager’s attention.
Craft your perfect resume in minutes
Get 2x more interviews with Resume Builder. Access Pro Plan features for a limited time!

Once your resume is done, a good way to finish it before sending it off to your prospective employer is to add a cover letter. This is a great opportunity to speak directly to the hiring manager and make a case for why you’re the best candidate for the job.
Remember, a cover letter should be fairly succinct. Try not to exceed more than 400 words — 250 to 300 is ideal. For more information and ideas, view our computer science cover letter examples.